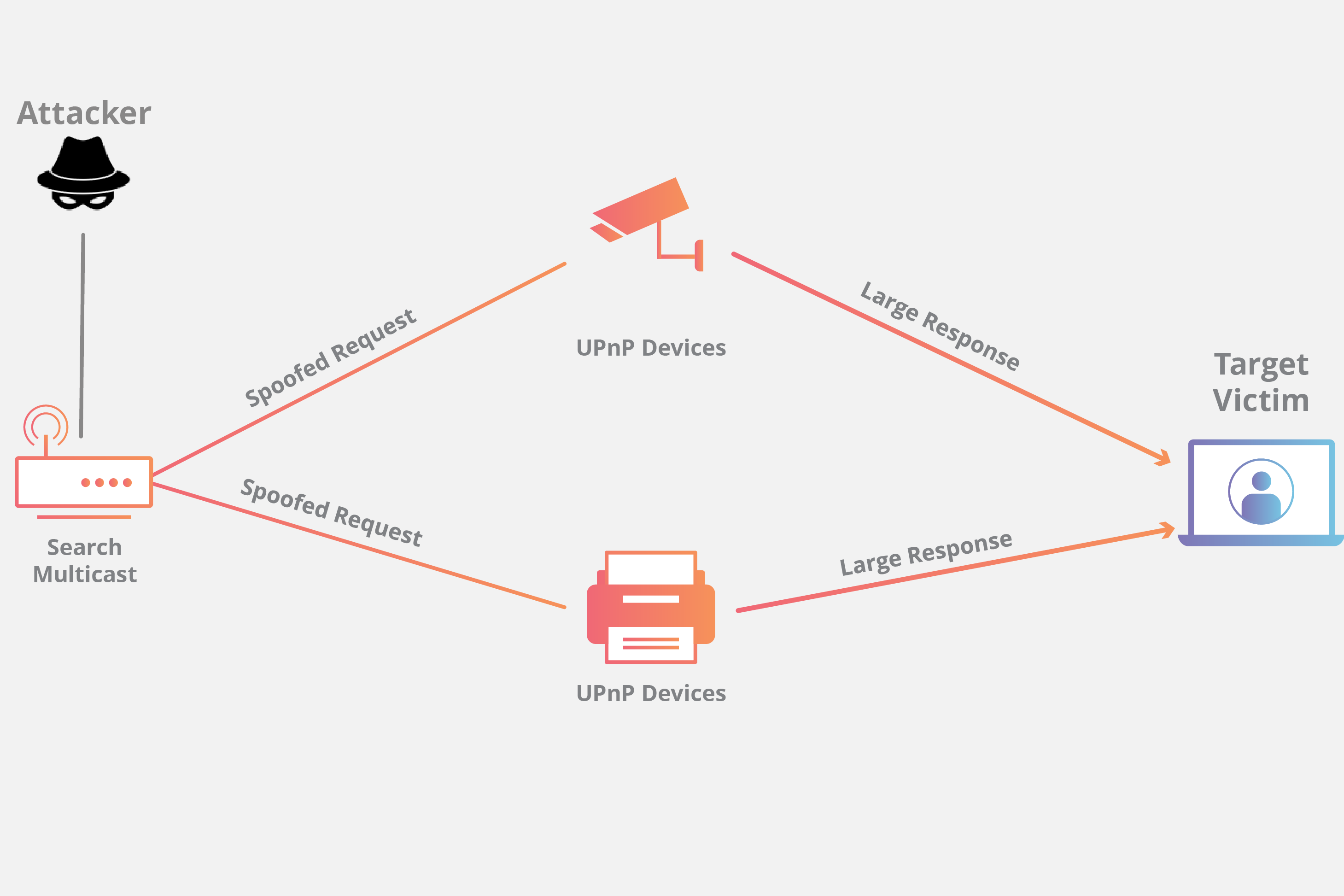
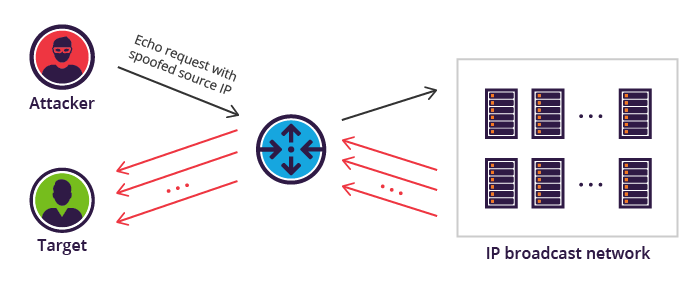
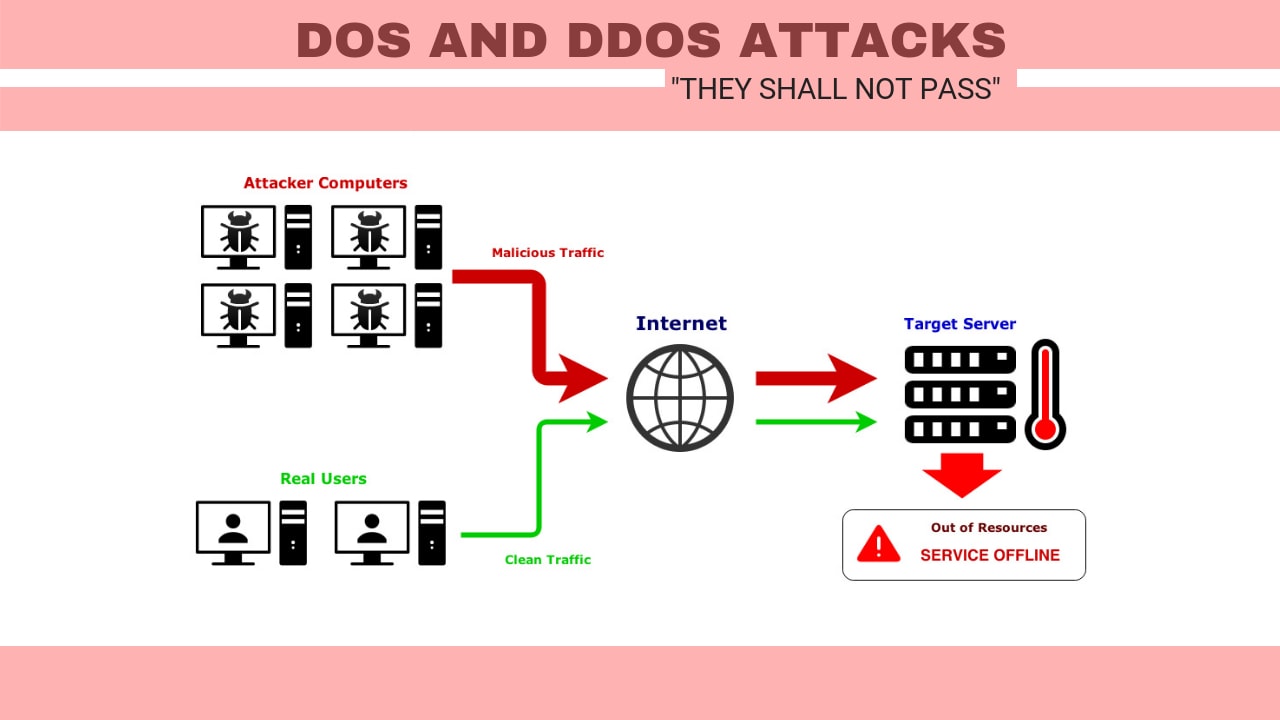
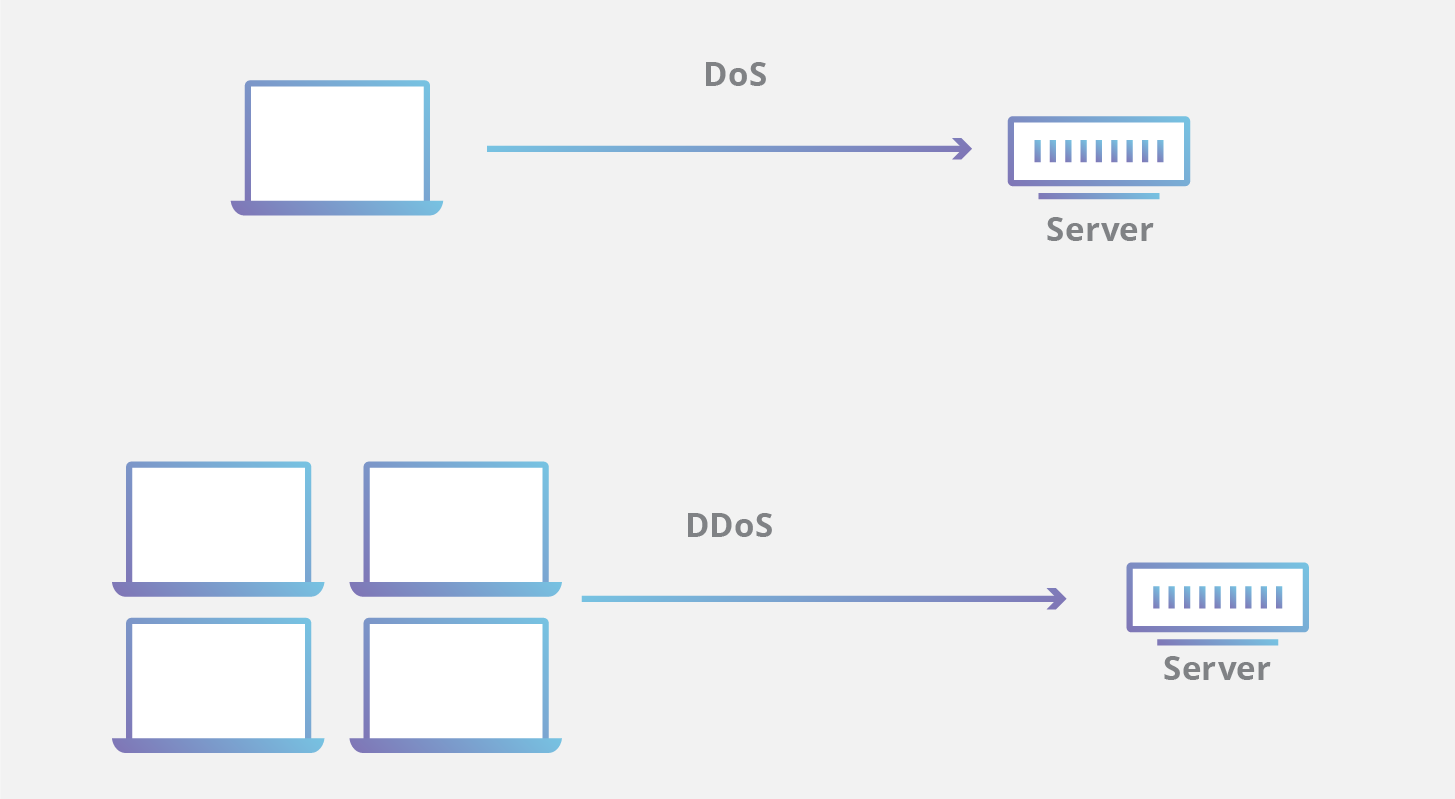
How To Do Dos Attack
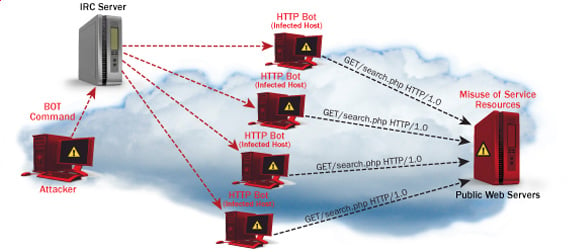
We can call bot to all these compromised machines that carry out the attack.
How to do dos attack. You just pick a system select an open port and then start sending lots of. A simple tutorial on how to perform dos attack using ping of death using cmd. Historically dos attacks were a primary method for disrupting computer systems on a network. Although you can t control when you might come under attack following the steps outlined below may help you minimize the impact of the attack get you on your way to.
Many major companies have been the focus of dos attacks. We can also call dos ping of death. Simple denial of service dos attacks are pretty straightforward. This is just for educational purposes.
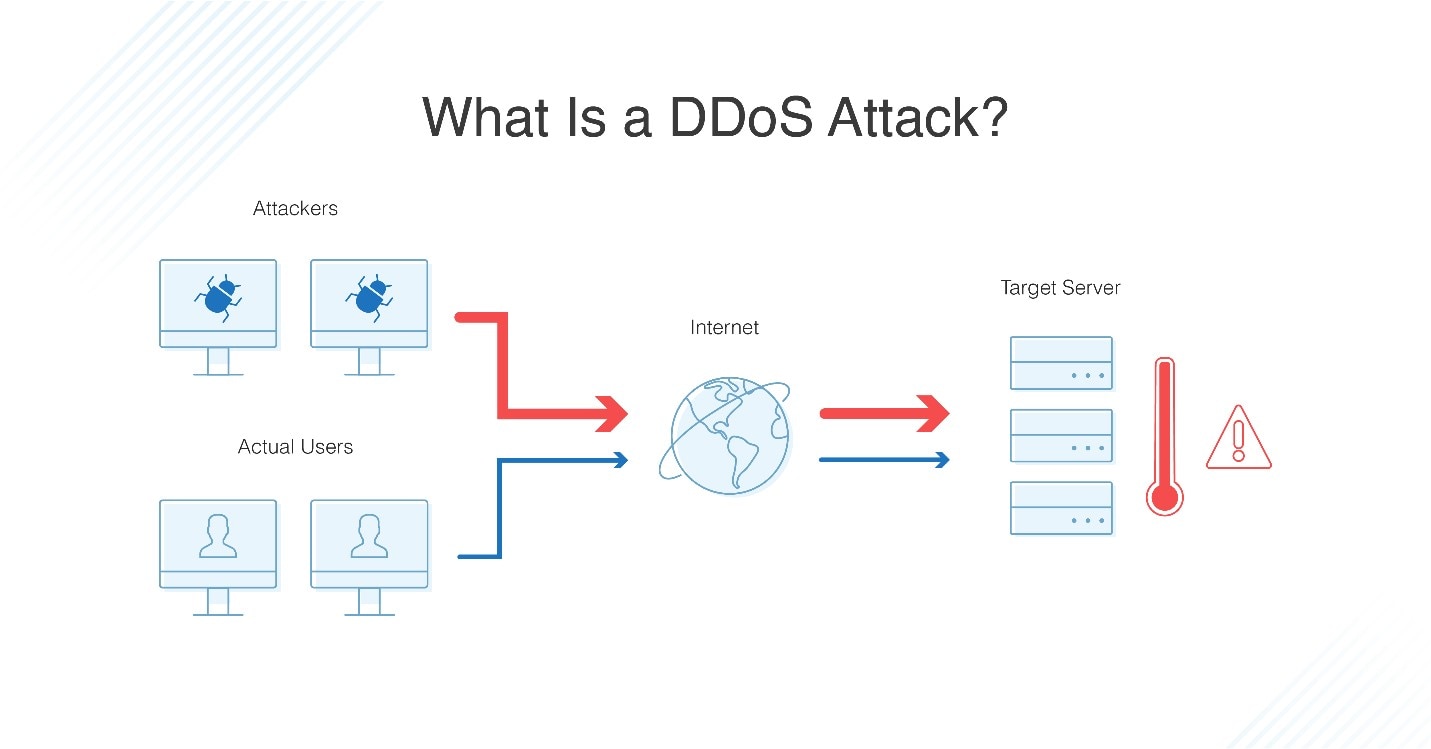
The only difference between dos and ddos is that the dos attack is carried out by one machine normally and ddos attack is carried out by many compromised online systems or computers. Dos attack by kali linux dos attack tutorial denial of service attack step by step with kali script. Because a dos attack can be easily engineered from nearly any location finding those responsible can be extremely difficult. The first part of this blog series discussed some of the steps you should take to prepare for a distributed denial of service ddos attack before it happens this post will discuss what to do now that you are under an attack.
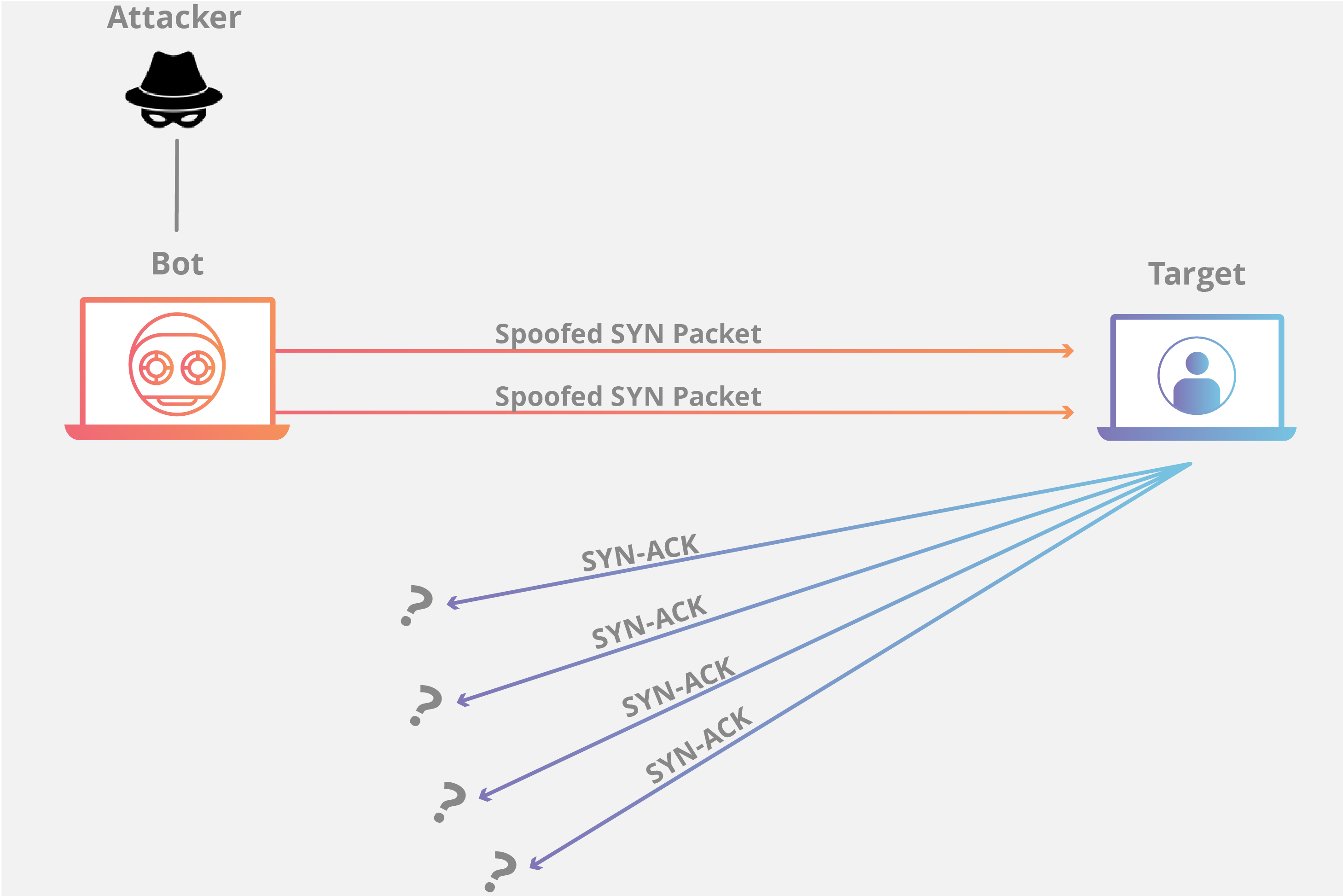
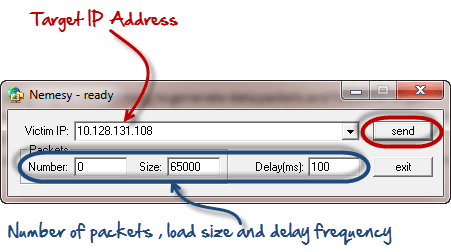
A dos attack is a denial of service attack where a computer is used to flood a server with tcp and udp packets. It s nothing great but you can use it to learn. Dos this type of attack is performed by a single host. In ethical hacking a ddos attack is often called stress testing.
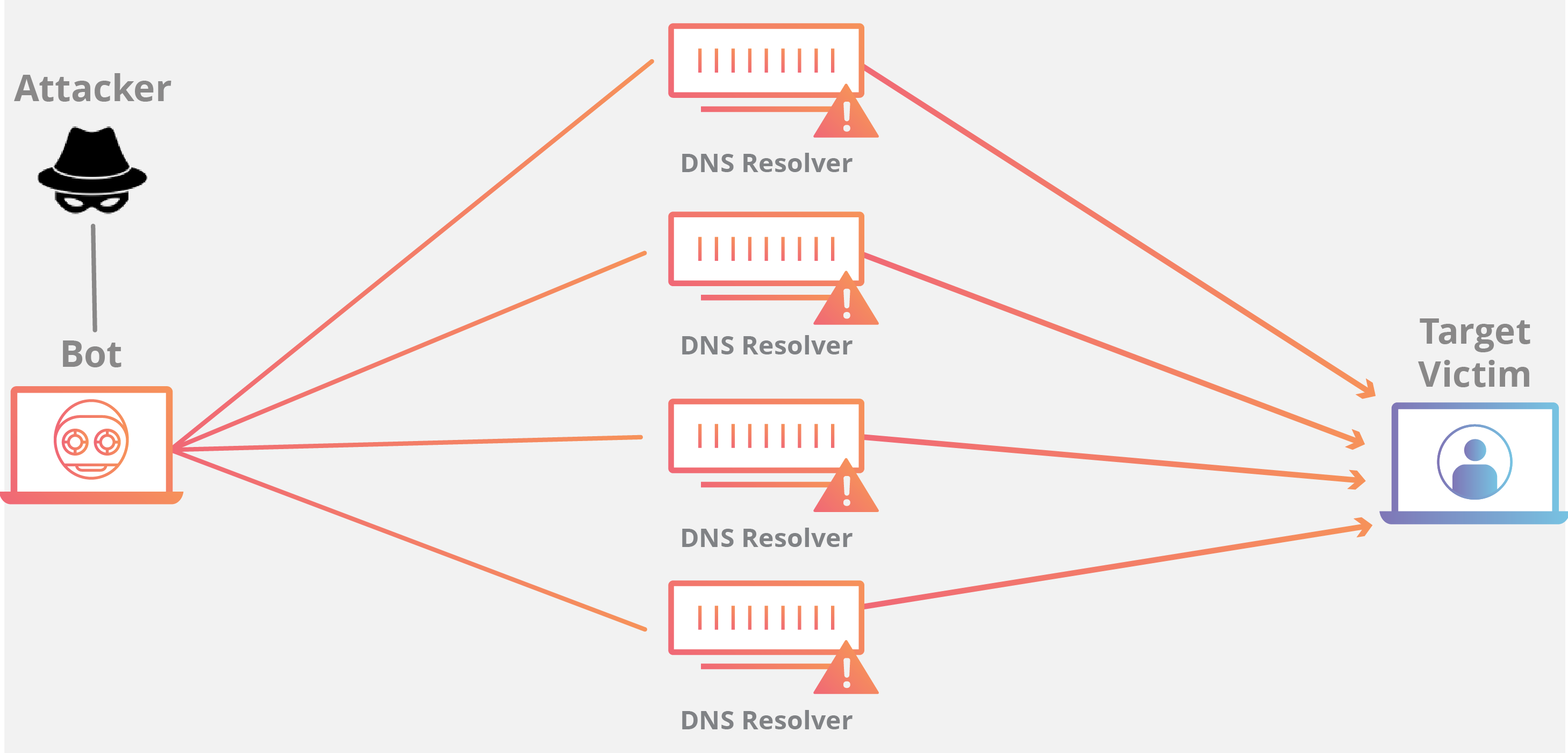
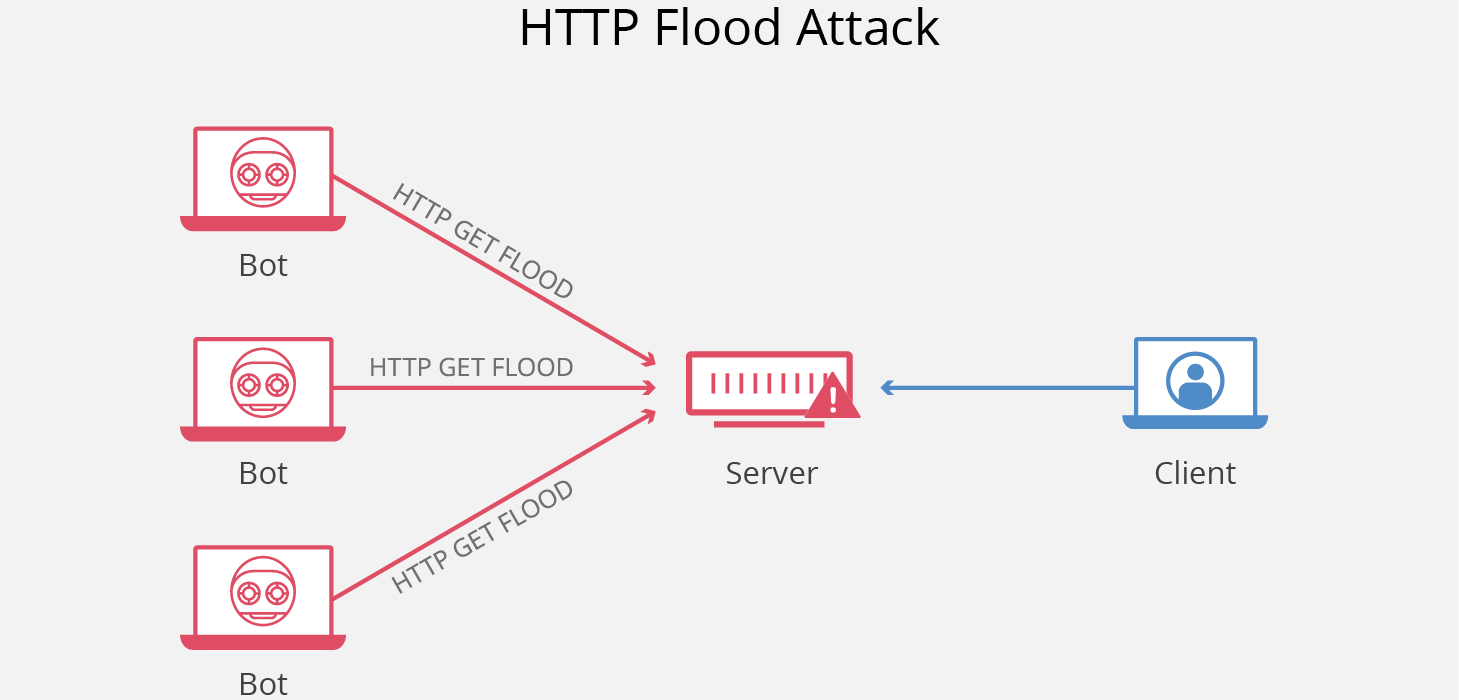
Let s look at how dos attacks are performed and the techniques used. Dos attacks originate from a single machine and can be very simple. A denial of service or dos attack is used to tie up a website s resources so that users who need to access the site cannot do so. Distributed dos this type of attack is performed by a number of compromised machines that all target the same victim it floods the network with data packets.
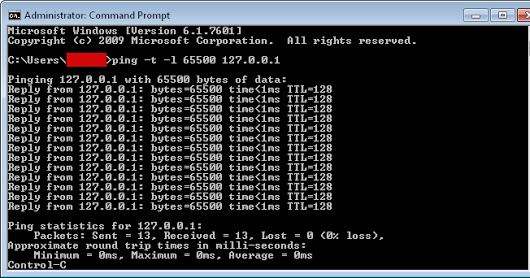
During this type of attack the service is put out of action as the packets sent over the network to overload the server s capabilities and make the server unavailable to other devices and users throughout the network. This attack is more powerful than dos attack. A basic ping flood attack can be accomplished by sending more icmp ping requests to a targeted server then it is able to process and respond to efficiently. When an attack is performed from multiple sources to one victim destination it s called a ddos.
Denial of service dos attacks are the precursor to ddos attacks. How dos attacks work.